I’ve recently completed the Bug Bounty Hunter job-role path on HTB Academy, which was a fun and challenging ride. Overall, I found it enjoyable and learned some new skills. Isn’t that always a plus? The content actually helped me better prepare for my most recent round of technical interviews. Even though these all sound like great outcomes, I will not be taking the CBBH (Certified Bug Bounty Hunter) exam associated with the path, and here’s why.
What is Academy and the Bug Bounty Hunter job-role path?
Academy is HTB’s relatively new learning program that offers a catalog of both offensive and defensive cyber security content. The courses, or modules, usually feature some pretty technical concepts and have several hands-on lab exercises along the way. There is normally a Skills Assessment at the end that tests your knowledge on the entire module with very little direction. The Bug Bounty Hunter Path is a specific job-role path made up of 20 modules that cater to that skillset.
As for the job-role path, it’s exactly what it sounds like. It prepares you for bug bounty hunting and web app pen testing work (emphasis on “web app” – there is no network, mobile, or cloud content). This means learning everything from what a bug bounty program looks like to discovering, exploiting, and reporting vulnerabilities. After completing the modules, you’ll be very familiar with using web app pen testing tools, like Burp Suite and OWASP ZAP, among others. You’ll also become familiar with the different types of web attacks such as SQLi, XSS, CSRF, SSRF, command injection, file uploads, and more. You don’t need to take this to start doing bug bounties or apply for that pen testing role, but it’s a good place to start if you’re just getting into cyber security.
Once you’ve completed the path, you’re eligible to take the CBBH exam for a shot at earning the certification. If you read the intro, you know that I have not and will not take the exam, so if you’re looking for exam details or pass/fail stories, this isn’t the post for you. What I do know is that the exam sounds very much like the OSCP exam in that you are given a lab environment and a chunk of time to find vulnerabilities as well as write them up in a report. You have a heaping 7 days to complete the exam. The intention here is to give you enough time to balance taking the exam with the rest of your everyday life.
Who is this content geared towards?
This content is geared towards individuals that already possess introductory knowledge of computer systems and/or cyber security who are looking to further their skillset and learn web app pen testing. Think of it as everything you need to know to start looking for common web security flaws. It can certainly help you prepare for a junior level AppSec analyst, threat and vulnerability analyst, or pen tester role. Experienced professionals can also benefit from this material, although I don’t think that they will get the biggest bang for their buck, which I will talk more about later.
There’s also another category of individuals that can learn from this content and that is web developers. I am not bashing web devs, but this makes sense as they have the means of accidentally introducing vulnerabilities into the software they write. Security is becoming everyone’s responsibility. Although they have different job roles, developers and security engineers work together to create and deploy secure software products. Possessing the knowledge taught in this job-role path will only make you a better and more security-conscious developer.

What were the pros of your overall experience with this path?
Some of the pros of my experience include:
- Great web hacking content; covers OWASP Top 10 – 2021 pretty well
- Tons of hands on practice opportunities
- Self-paced and organized content structure
If there is one thing that this job-role path does well, it’s that it incorporates a lot of useful web hacking content and techniques in one place. It doesn’t cover everything in the web hacking world, but it sure covers the baseline and then some. There’s almost an individual module for each of the OWASP Top 10, and if there isn’t, it’s covered in some sort of way elsewhere. This is more than enough to get you started as a successful bug bounty hunter or web app pen tester.
What have to be the most important parts of each module are the hands-on labs and Skills Assessments. It’s one thing to be lectured on technical concepts, but to actually apply what you learned is even more valuable and completes the learning process. This is especially important when it comes to pen testing because there are limited opportunities to get your hands on the keyboard and practice ethical hacking. When it comes to pen testing labs, HTB has established a name, and their experience in creating useful and responsive labs really shows in the Academy modules.
Not only is the variety content a huge upside of taking this job-role path, so is the delivery of the content. The Academy is structured so that you can take whichever module you want in whatever order, at your own pace. Personally, I took them in the order that they were listed, but there is nothing stopping you from mixing it up. There’s also nothing stopping you from taking a week-long break, other than you’re paying a monthly subscription rate. I maybe would have enjoyed seeing some videos mixed in, but they do split up the content enough with exercises so that you aren’t reading too much at one time.
What were the cons of your overall experience with this path?
Some of the cons of my experience include:
- No option to keep moving within a module if you are stuck
- Some modules are lacking and some are just plain too difficult
- The writing style bothered me; more QA needed
One of the most frustrating parts of taking any module in HTB Academy is that you can’t move on to the next section until you’ve answered the current section’s questions correctly. So, if you can’t manage to get your exploit working or maybe you’re just not entering the answer in the correct format, you’re stuck there until you figure it out. There is one module in particular, Broken Authentication, that was just awfully difficult. By this, I mean that the difficulty actually distracted me from the course content. As an example, if I recall correctly, there are exercises where you need to brute force or forge session tokens. The complicated formatting of timestamps, multiple layers of encoding, etc. were too challenging and unrealistic that they distracted from the underlying concepts.
Now, there are different options to get some help along the way. Those are the HTB forum pages, the HTB community, and the HTB Discord. The forum pages usually have existing discussions around the biggest blockers to students, and the community and Discord always have friendly folks that will give you a nudge if you ask nicely.
Another downside to my experience was that a few of the modules were still being built out as I was enrolled in the job-role path. This ended up not being a huge deal for me, as I was far enough behind where the modules were finished before it was my time to take them. However, there was that initial guessing where maybe I was going to hit a roadblock. They only displayed “coming soon” in the section banner, so how was I supposed to know how soon that was? This also means they were freshly released modules and I would be one of the first to take them, which brings me to my next point.
While some modules were great, some were either lacking in content or terrible to read. If I had to guess, most of the sections were written by different people, and possibly by some of who are not native English speakers. There is nothing wrong with any of this, in fact I would not expect one person to write the entire path. However, there should have been more effort put into quality control and the overall flow between modules. Each time I started a new module, it was a different experience from the last. Some were pretty decent, while others had typos, grammar mistakes, or were overall lacking in content. My least favorite were the unnecessarily wordy modules, where I found myself saying “oh dear” out loud and skimming word vomit for something to actually grasp ahold of to learn. I did not sign up to read college essays.
Will you just tell us why you won't take the exam already?
Okay, so I originally went into the Bug Bounty Hunter Path not really planning on taking the exam and just seeing where it takes me. After completing all of the content, I decided to stick with my decision for a few reasons.
1. CBBH is not a widely recognized cert (at least not yet)
Personally, I don’t see the value in getting this cert for where I am at in my career. I don’t think the CBBH is currently on anyone’s radar. I have yet to see a job posting that specifically lists it as a requirement or a “nice to have”. While I do think it has potential in being more widely recognized, it has some work to do to get there. There are just too many other good pen testing certs out there created by some very reputable companies, like OffSec and SANS, and CBBH doesn’t really stand out from them in any way. Certs like OSCP and GPEN are a part of every tech recruiters lingo and they hunt for talent with those letters in their resume or LinkedIn profile.
This isn’t to say that CBBH is a bad cert. There might be a time and a place for it if you are just getting started with cyber security or beginning to pivot into pen testing and bug bounty hunting. You’ll need to decide if the reward is worth the time and money spent.
2. I don’t think it’s worth the investment to me
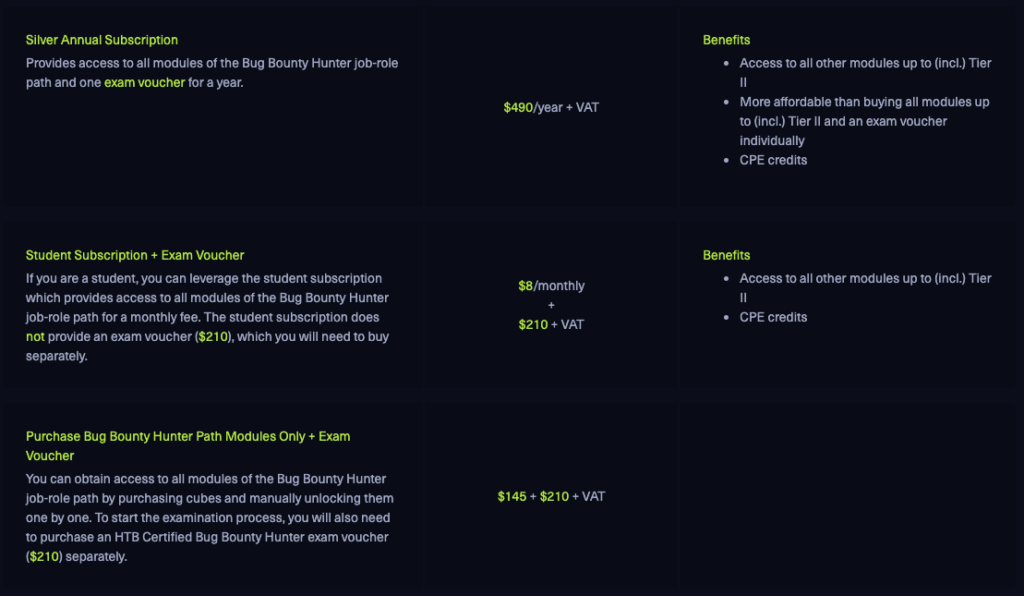
Let’s quickly break down the cost of earning the CBBH cert. HTB gives a nice summary of the purchase options.
You can get the Bug Bounty Hunter Path content and 2 exam vouchers for as little as $355, maybe even less if you have a .edu email address. This is actually quite cheap compared to other certs, but going back to my first point, the other certs are more reputable and carry more weight. In my case, I still have a .edu email address and I am able to get an Academy subscription for fairly cheap. I’ve probably spent somewhere between $50-$70 to complete the path and that’s good enough for me. Yes, I would now only need to buy the exam vouchers and sign up for the exam. I realize that I’m very close to the finish line. That being said, money is just one piece of the picture.
Not only do you need to evaluate the monetary cost, but you also need to consider the time investment. For me, I went at a leisurely pace and complete the content over the course of 5-6 months with roughly 60-80 hours spent total. I had quite a few breaks in there, and like I said before, I didn’t really plan on taking the exam so there was no rush. My timing is probably a lot different than someone else who is serious about studying for the exam.
When it comes to the exam, you are given 7 days to access the lab environment and complete all of the tasks given to you. I realize that the 7 days accounts for sleeping, eating, and going about your daily life, but I also don’t have a week right now that I can set aside to do that. Maybe I’m complaining too much, but this seems like a large expectation and commitment. It’s not new for pen testing certs to be demanding of one’s time. OffSec is notorious for having 24-hour, 48-hour, and even 72-hour exams. Currently, I just can’t justify setting aside a 7-day window to work on and stress about something that will give me very little return.
3. I’ve got other priorities
Tying back into the previous points, I’ve got other things that I need to dedicate my resources to. It might be a different story if I didn’t have other goals and ambitions, but I feel that my time and money are better spent elsewhere. This includes other certs and cyber content that I’m pursuing, as well as just my personal life and hobbies. I’m satisfied with the amount of time and money I’ve put into the Bug Bounty path for what I’ve all learned and that’s where I’m comfortable leaving it.
Ending Remarks
Generally speaking, my experience with Academy and the Bug Bounty Hunter Path were positive. I am happy with what I’ve accomplished and where I am departing on the certification track. I can definitely say that I do not regret the time I’ve spent, as I’ve learned a few things along the way. Although I’ve paused my subscription for now, I plan to come back to the Academy in the future to take a look at some of the other modules.
I would recommend the Bug Bounty Hunter Path and CBBH for anyone who is brand new to cyber security, pen testing, or bug bounty hunting, especially for students or someone with access to a .edu email address. While the CBBH may still need some work, HTB is still a master at creating content that teaches you some very valuable hands-on skills. They will continue to be a name in the cyber security training industry and I can’t wait to see improvements to their current content as well as what they have in store for the future.